Use Case #2
USE CASE #2
Cyber security for connected medical devices and mobile applications
Aim: To validate SECANT’s efficiency to deal with cascading effects of cyber threats and with propagated
vulnerabilities in connected healthcare infrastructures, as well as in remote healthcare settings.
Scenario to be demonstrated: Scenario to be demonstrated: This pilot use case involves the installation of the SECANT platform in the servers
of KI’s LIME (Learning, Informatics, Management and Ethics) Department, which is one of Europe’s premier
medical research institutes with strong collaboration with other hospitals and medical institutes in Northern Europe.
KI’s LIME Department provides access to mobile applications and systems that are hosted in the LIME servers, and
which are tasked with collecting information and medical data from different groups of patients of the Danderyd
Hospital in Stockholm for research purposes. More specifically, the first one is a mobile health research system that
enriches the follow up information coming from various medical devices regarding patients diagnosed with cancer
in order to support methodological and clinical studies on patient reported outcomes such as Quality of Life (QoL),
well-being, symptoms and satisfaction with care in different diagnoses and settings.
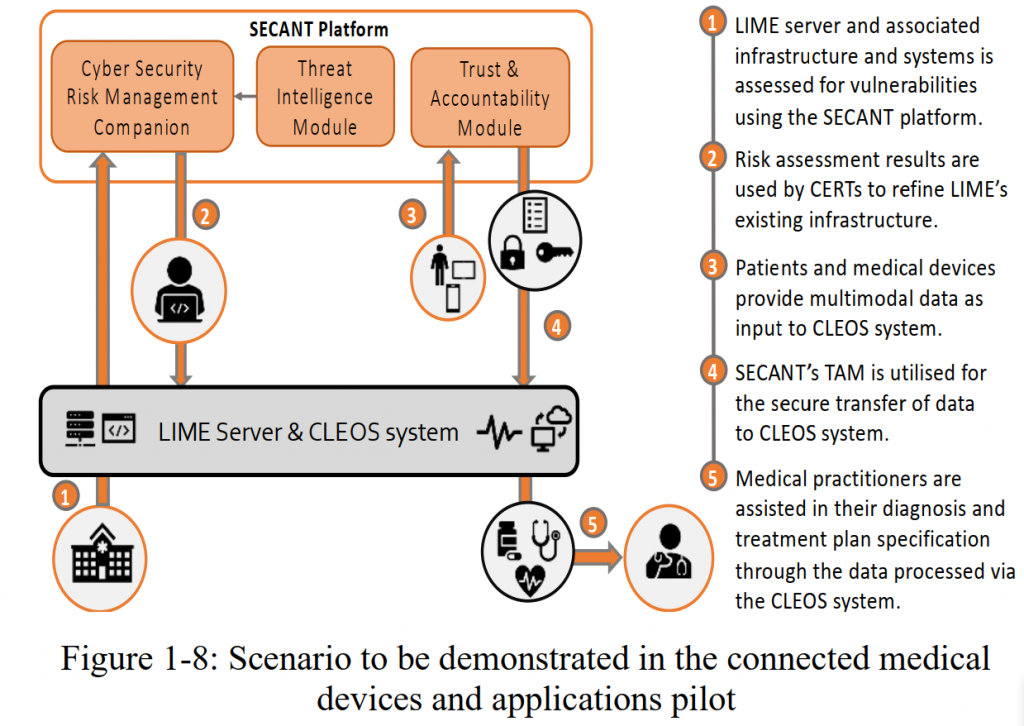
The second system, called
Clinical Expert Operating System (CLEOS, https://cleos.ki.se) is a primary care clinical collection system. CLEOS
automates the collection of follow-up patient data regarding known active medical problems, and standardizes the
evaluation of the outcomes reported by the
patients by using appropriate laboratory
measurements. In this pilot, the various
modules of the SECANT platform depicted
in Figure 1-8 will be tested for their efficacy
in (i) identifying and isolating software
vulnerabilities in the LIME ecosystem and
(ii) in securing the whole lifecycle of
research-based healthcare applications and
systems and data collection-storing-sharing,
while enriching the knowledge in designing
security software and forming security
practices on developing and implementing
software and hardware components. PUC2
will also validate the ability of SECANT’s
Threat Intelligence Collection Module in
capturing cybersecurity threats, incidents and
anomaly traces.
Sign up for SECANT Newsletter

This project has received funding from the European Union’s Horizon 2020
Research and Innovation programme under grant agreement No. 101019645.
Disclaimer
The content of this website reflects the Secant consortium view and the European Commission (or its delegated Agency INEA) is not responsible for any use that may be made of the information it contains

